Adware / madware
Adware and madware (mobile adware) are everywhere and usually do very little damage to your device. They are usually designed to simply display frequent adverts for which the creators get paid for views and clicks. Adware is very annoying and is usually loaded onto a device through downloading of "free", trial or ad-supported software.
Antivirus / anti-malware
Good antivirus software should protect your device from most of the threats listed on this page, but you can also install separate anti-malware software that targets specific threats such as adware, ransonware and others. Good antivirus software should be paired with a strong firewall for better protection.
Bot / botnet
An Internet bot is a piece of malicious software that runs automated tasks over the Internet. A botnet is a number of Internet-connected devices, each of which is running one or more bots. Botnets are often used in DDOS attacks.
Browser hijacker
This is a type of malware that takes some control over what your web browsers do. This includes redirecting any attempts to access your normal search engine to another location where criminals gain income from either search results or adverts on the pages. A browser hijacker can also prevent you from accessing genuine antivirus vendor websites and will often send all of your website data to the cyber criminals behind the hijack.
DDOS
Distributed Denial Of Service - This is a type of cyber attack where a large number of computers are used to direct enormous volumes of traffic at a website or service. The website or service is so busy dealing with this traffic that genuine users and customers cannot access it.
Firewall
A firewall is a piece of software or a physical box that monitors traffic into and out of your network. They are designed to work with a set of rules that prevents malicious access to your devices.
Hacker
There are various types of hacker (whitehat hackers work on behalf of organisations to find and fix security risks in their systems) and most of them have some kind of malicious intent. They will break into services, systems and accounts for some sort of financial, social or reputational gain.
Keylogger
A keylogger can record all of the keypresses that you make on either a physical or onscreen keyboard. This information is then sent to the cyber criminals who can see when you type in any usernames and passwords on your device and for websites you visit. They can now use this information to access your accounts.
Malware
This is the generic term for all of the other malicious software listed on this page.
Phishing
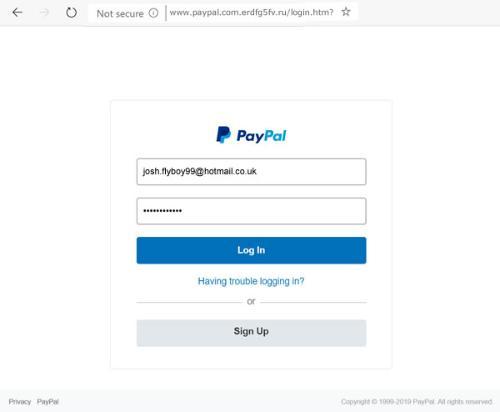
Phishing is an attempt to obtain sensitive information such as usernames, passwords and credit card details by disguising itself as a trusted web link or attachment in emails, social media posts and even text messages. See Email Security for more information.
Ransomware
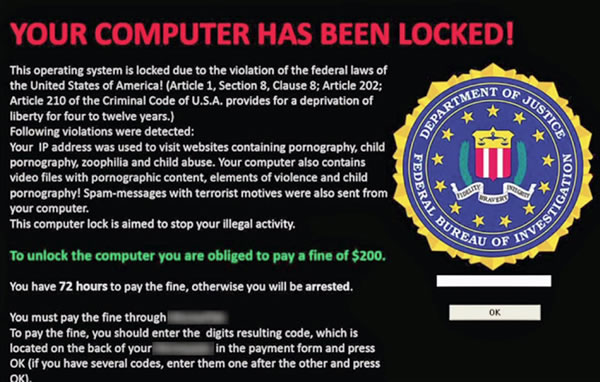
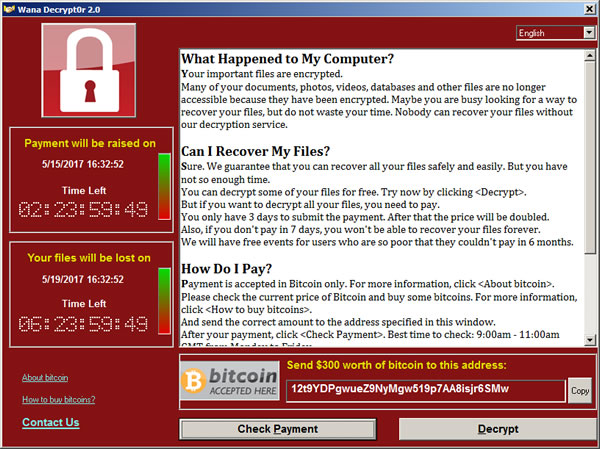
Ransomware is a type of attack that locks all of the files on your device until you pay a ransom. See "My computer says a must pay a fine or a ransom" further up this page.
Rogue antivirus software
This is software designed to appear like legitimate security software and misleads users into believing their computer is infected with a virus, with the intent of tricking them into paying money for a fake malware removal tool. The fake malware removal tool can even introduce real malware onto the computer
Rootkit
A rootkit is a type of malware that buries itself deeply within your operating system. This makes them very hard to detect and provides them with complete "root" access to you entire system. A rootkit can rewrite antivirus software so that it ignores the threat. A cyber criminal now has access to everything you do on your device.
Spyware
Spyware spiess on you and all of the activities that you carry out on your device. A cyber criminal can see your logins, passwords, the webpages you are visiting, the videos your are watching, the chats you are in and even the view from your webcam (front and rear cameras on an infected mobile device).
Trojans
These are very dangerous and often disguise themselves as legitimate software. A trojan can allow a cyber criminal to take complete control of your device without alerting you to their presence. A trojan infected device can also be used as part of a botnet to perform DDOS attacks.
Virus
Computer viruses extremely varied and are normally designed to simply destroy files and wreak havoc.
Worms
A computer worm is a self-contained, self-replicating computer program that spreads to other files or other computers. Worms can contain most other types of malware.
Some of the definitions on this page were derived from: https://www.askboard.com/tech/comprehensive-list-of-malware-types/